INTERVIEW | CRYPTOME: 1996/2016 [TEXT-ONLY VERSION]
❝ H C-(M) of Tecno|Grafia[s] has been immensely generous proposing and hosting an in-depth dialogue to mark Cryptome's first two decades, 1996-2016. We welcome this unprecedented exchange for its forward momentum towards the future.
[...] The results make clear that Tecno|Grafia[s] platform is distinctive, engaging and important contribution to ongoing debates.❞
- Deborah Natsios and John Young, Cryptome _2016
"Cryptome welcomes documents for publication that are prohibited by governments worldwide, in particular material on freedom of expression, privacy, cryptology, dual-use technologies, national security, intelligence, and secret governance -- open, secret and classified documents -- but not limited to those. Documents are removed from this site only by order served directly by a US court having jurisdiction. No court order has ever been served; any order served will be published here -- or elsewhere if gagged by order. Bluffs will be published if comical but otherwise ignored. "
〼 IN JUNE OF THIS YEAR CRYPTOME.ORG TURNS 20 YEARS OF RELEASING DOCUMENTS ONLINE. THE DEFINITIONS FOUND IN THE MAINSTREAM MEDIA DOESN'T NECESSARILY UNDERSTAND THE WIDE SCOPE THAT CRYPTOME HAS ESTABLISHED THROUGH THE YEARS.
HOW WOULD YOU DEFINE THE FUNCTIONS OF THIS EXTENSIVE PLATFORM?
CRYPTOME: Cryptome's mission statement confirms we spend a lot of time poking holes in the exceptional privileges granted to the cult of security at the scale of the nation-state. Our tactics are as varied as can be expected when artists confront such a formidable juggernaut. Initiatives range from hosting and archiving an eponymous online library in the name of banned information, to engaging networked debates, to practicing a critical cartography and a counter-market approach to licensed architecture. These shifting maneuvers are synergetic rather than reductive. Wry humor and irreverence sometimes help set the tone. We happen to hold political satire in high esteem.
Embedded in Cryptome's synergism is the understanding that privileging security at the nationalist scale is usually achieved at the expense of policy commitments to security at the scale of the individual. Dual-use technologies with military and civilian applications offer a false rapprochement between two incommensurable scales. Security at the scale of the person is built upon the right to privacy that endows autonomous personhood in all those relational social dimensions David Lyon reminds us that
Privacy's relational dimensions are vital predicates for engagement in social space, and, not least for a robust democracy, the risky but crucial public space of protest and dissent. Self-knowledge and self-rule go hand in hand.
It's been noted that at the same time as the State increasingly demands the individual be totally visible to it (through mass surveillance) the State increasingly demands that it be invisible to the individual (through secrecy). Cryptome's incremental daily practices of reverse-engineering these asymmetric visualizations are small-scale acts of public service in support of the information equality we believe undergirds self-rule. Cryptome Eyeball Series taps into open-source satellite imagery to flip the national security gaze back against itself.
Each raw document offered by the Cryptome library is thought of as a public good invested at the scale of informed individual agency. This is meant to counter the anomic scales of Big Data algorithmics and analytics. Communities of engaged readers complete the collection's circadian feedback circuits 'from below' with ongoing contributions cycling via Twitter and other non-hierarchical platforms for exchange. Our generic A. signifies the contributor who requests anonymity. Some contributors have been forwarding material for twenty years. We think citizen declassification initiatives like those triggered by Chelsea Manning and Edward Snowden are welcome exemplars of robust fair use and the reclamation of information on behalf of the public domain and an equitable information ecosystem.
Cryptome's archive of around 101,000 files spanning 1996-2016 is currently backed up on
a diminutive 64 gigabyte USB flash drive weighing around 4 grams, measuring 38.9mm X 12.3mm X 4.5mm. Authenticated drives are occasionally shipped by snail mail across the material time and space of global postal supply chains to supporters throughout the lived world. Recipients provide offshore backup and redundancy by mirroring the library through the lens of their active engagement with the information, no questions asked.
As licensed architects based in New York City, John Young and I are mandated by code to give precedence to issues of public Health, public Safety and public Welfare (HSW). What does this public mandate really mean when deployed in the free-markets of the ascendant global city? HSW's infrastructure of public goods, embodied at the visceral scale of the individual, are devalued by some ranks of our profession because of the relative cultural invisibility of backgrounded infrastructure. We regret starchitecture's penchant of market-driven, scenographic branding. That glitzy approach perpetuates an inherently supply-side, trickle-down theory of consumption of public goods as a kind of non-renewable resource. The eye devours and exhausts the supply during repeated acts of false consciousness. Glossy brochures -- the industry standard for marketing architectural services -- are unintended chronicles of this unfortunate depletion. When asked for our brochure, we likely pay a heavy professional price by occasionally directing inquiries to Cryptome.org.
We like to think of HSW infrastructures, like those constituted in the public library, as underground wedges for insurgent opportunity. This is especially the case in the context of the production of code-compliant places of assembly, which, like the library, should be fundamentally democratic sites. Issues of personal security and insecurity in the lived urban world, informed by HSW values invested in over 400 low-profile architectural interventions we've consulted on in the metropolitan NYC area (including some brick-and-mortar libraries) provide Cryptome's ethical point of reference against the inflation of national security power and privilege.
CRYPTOME: As an introductory gambit, we'd like to point out that the layered urban context that frames our perspectives on HSW security derives in many ways from uncertainties of our own unusually peripatetic upbringings. Mobility across shifting landscapes was for each of us the loom shuttle that threaded narrative at overlapping scales of being grounded in local and global childhood worlds. We track some of these swarming border-crossings in our cartographic works.
As a youngster, John transited through 35 or more towns and rural locales of Central and West Texas while his father followed seasonal work as an itinerant laborer in cotton agriculture, rock quarrying and oil rig construction. They lived in the rough or in migrant worker sheds. They challenged foremen who tried to undercut wages by under- weighing 100-lb and 50-lb burlap sacks of cotton father and son dragged behind them while hand-picking along the rows. Rural elementary schools were accustomed to the episodic comings and goings of such transient child labor. John was taken out of school at 14 to help support the family full time, and by 17, like many young men from similar backgrounds, gained entry into the US Army. His construction skills placed him in the Army Corps of Engineers and he was abruptly transported 5000 miles away to the divided Germany of the Cold War era.
My own childhood border-crossings intersected the Cold War in capital cities of Europe, Asia and South America with a parent who served as cold warrior during what is referred to, with irony in some cases, as the Pax Americana. We occupied the more clandestine enclaves of diplomatic corps extraterritoriality being negotiated by the era's East-West polarizations. Secrecy was the lingua franca of my childhood experiences of the putative Pax. At the same time, our Greek ancestry admitted us into displaced communities of the worldwide Greek Diaspora. This overlaying of covert and diasporic geographies camouflaged nomadic terrain that was continuously shifting.
I keep a stained, typewritten leaflet as reminder of the tar bomb thrown at our house in Buenos Aires that reads in part: “Fuera politica del imperialismo YANQUI de intervención en los paises de LATINOAMERICA.” Even after the rout of the French at the battle of Dien Bien Phu, the French colonial convent school in Saigon where I began my education continued to teach the pedagogy of French Empire. Nuns were stunned when one of their star Vietnamese schoolgirls abandoned her subject position in the imperial schema to join Ho Chi Minh's anti-French Viêt-minh liberation movement.
The Cryptome library makes pretty clear John Young's and my youthful itinerancy did not end up producing a genre of leisure literature devoted to the consumption of world travel. Instead, Cryptome dedicates itself to bottom-up strategies for borderless information equality. We address issues of security and insecurity at the scales of larger worlds compressed into New York City's heterogeneous metropolitan milieux. We explore more insurgently democratic trajectories of information access than we ourselves experienced during somewhat furtive upbringings.
In the information age, of course, all pathways to the information-rich lived world run through the gauntlet of the politics of information. That gauntlet is populated along either side by an alliance of aggressive corporate and government agents who stake interlinked claims on informational property. High value is given to national security information. As with running all gauntlets, Cryptome finds evasive mobility is key to emerging reasonably intact.Tecno|Grafía[s] is right to conclude that media efforts to pin down or define Cryptome miss the mark of what we hope is a moving target. Cryptome seldom cooperates with mediated attempts to fix our evasive travel itineraries along well-marked, more heavily surveilled routes of a branding economy that captures identity in order to fix valuations for media products within well-exploited markets.
We recently produced an animated scroll of the full Cryptome index 1996-2016 for a talk on information policies and politics at Pratt Institute School of Information in NYC. With its 50-minute runtime, the scrolling index is a decidedly non-wayfinding map. Instead, it recapitulates the flowing time and space of two decades of Cryptome's information politics as a kind of borderless textual liquifaction that is hard to pin down.
Cryptome continues weaving youthful narratives that became formally problematized during our respective undergraduate educations. We each ended up at graduate architecture schools, but before that, John completed an undergraduate philosophy degree with a thesis on existentialism that proposed an aesthetic theory grounded in Sartre's work. Sartre's notion of the authentic project is arguably present in the Cryptome library.
And I, after becoming engrossed in the contrarian frameworks of non-Euclidean geometry, completed a mathematics major with research on transfinite numbers, an area of set theory that considers the meta-finite continuum. Negating Euclid's fifth parallel postulate and recognizing many infinities were very liberating logics.
John and my problematiques somehow touched on ontological and epistemological aspects of childhood fugitivity that cast doubt on certainty, finiteness, fixity and a priori essentialist categories. These challenges to traditions of taxonomic diagnosis that fix nomenclature and classification continue to resonate in Cryptome's critiques of rigidly abusive classification regimes.
〼 AS A "POLITICALLY INCORRECT" PROJECT, IT'S INTERESTING HOW CRYPTOME CONFRONTS US GOVERNMENT LAWS, BUT THEY ARE NOT THE ONLY ONES WHO HAVE TRIED TO SHUTDOWN THE WEBSITE IN THE PAST.
MANY PRIVATE CORPORATIONS LIKE MICROSOFT, VERIO OR YAHOO, NEED TO CENSOR CONTENTS THAT PROVIDE IMPORTANT INFORMATION ABOUT THE RELATIONSHIP BETWEEN THE USER'S PERSONAL DATA AND ESPIONAGE STRATEGIES, WHAT ARE THE DIFFERENCES BETWEEN GOVERNMENT STRUCTURES AND PRIVATE CORPORATIONS INTERESTS?
CRYPTOME: Cryptome recognizes attempts to censor sites that support information equality as being virtual variants of privatization projects that target and constrain public space as a viable HSW infrastructure and public utility. As intensely social locations, public spaces are knowledge ecosystems that are materially crucial to robust democratic practice and the public sphere. Of course, these are not welcomed by the proprietary mindset of government-corporate alliances we see consolidating around us.
A public domain for information equality has no place in the information economy's highly proprietary circuits of corporate production and consumption. Instead, the rise of government-corporate alliances means the surveillance state has successfully colonized the information economy's most prized natural resource: endless corporate feeds of proprietary data and metadata that track the minutiae of consumer desire.
Corporate privacy policies bundled with “free” apps and services lure consumers into willingly relinquishing their most vital and valuable flows.
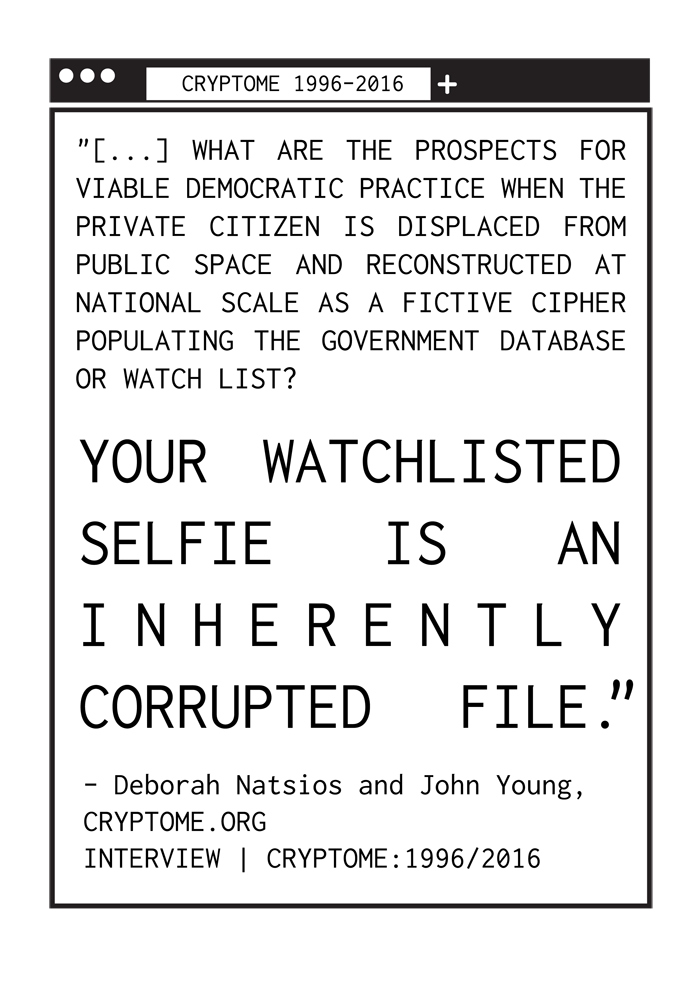
Authorities may access these private flows illegally, through court order or both in the name of a national security state of emergency. Corporate compliance guides have become standard office manuals to instruct staff on how to cooperate with law- enforcement subpoenas that demand consumer data and metadata. What are the prospects for viable democratic practice when the private citizen is displaced from public space and reconstructed at national scale as a fictive cipher populating the government database or watch list? Your watchlisted selfie is an inherently corrupted file.
Cryptome's intensive mobility as pedestrian architects traveling New York City streets always yields compelling local knowledge of HSW components embedded in dense urban infrastructures. Such visceral experiences of the lived city revitalize personhood and challenge the digital colonizing of our selves being captured by database analytics and the carceral watch list. We highly recommend such pedestrian constitutionals – in every sense of that freighted word. Tactical mobility reconstitutes our reading of the city as a public library evolving in 4D time and space. The city as historical archive of public knowledge provides dynamic foundations for collective memory, information equality and innovation towards future outcomes.
The materiality of our urban archive announces itself in resilient narratives of concrete, brick, glass, steel, brownstone and, more recently, fiber optic cabling. Songbirds broadcast vigorous signals from branches of oak, callery pear and cellphone antennae. Engaging a politics of personhood on the street requires vigilance and tactical mobility. Pay attention to the planned 10,000 sidewalk kiosks that are supplanting NYC payphone infrastructure with Wi-Fi offering free high-speed Internet service to anyone within 45 meters. This city-wide grid of ubiquitous sensors has the privacy-invasive technological and political capability to siphon and archive ambient data streams without citizen consent. Civil liberties may be suspended during states of emergency. The grocery list called into your 'butcher' may contain actionable keywords.
In recent decades, John and my local ambulations in NYC have provided stark views onto the near-completion of the market-driven project to erase public space. We don't keep a car, and I never learned to drive. When not being swept along mass transit as members of the metropolitan throng, we reconnoiter kilometer after kilometer of the lived city intimately as peripatetics of the street, as walkers of the parkland and evolving waterfront.
From our perspective on the street, we can confirm public access is being categorically denied by sovereign and neoliberal spaces of exclusion. Paywalls and curtain-walls enforce prohibitions. Once affordable 19th century immigrant tenements on the Lower East Side are now out of reach to other than upscale occupants. The university's elite classrooms are increasingly available only to those with the deepest pockets. Luxury developers forced by the city to provide minimum units of affordable housing in new high-end towers design separate “poor doors” to relieve the moneyed class from having to share entrance lobbies and elevators with lower-income neighbors.
The public may be granted access to private amenities like Zuccotti Park in exchange for increased for-profit development densities, as during the Occupy movement. But these spaces are policed by private security officers and highly restrictive rules of behavior. Token public art installed in privatized plazas are anodyne substitutes for prohibited political speech and agitated assembly.
Social stratification in the city of cognitive-cultural capitalism described by Allen Scott has exacerbated New York City's segregated zones of absentee oligarchs and decimated working and middle classes. The architectural profession at large, and formalist starchitects in particular, are heavily implicated in these polarizing activities. At the same time that risk assessments privilege some urban systems as Critical Infrastructures within the states of emergency promoted in national security frameworks – often camouflaging data spies like Wi-Fi kiosks – systems that support urgent HSW needs are devalued and defunded. Who are the real beneficiaries of privacy-busting 'smart-city' urban data capture initiatives?
The profound asymmetry between personal security and national security is the skewed calculus that drives us to challenge pernicious acts of spatial closure through Cryptome's ongoing support of prohibited documents and support of prohibited acts of conscientious disclosure. Public access to the library of decrypted information relating to all phases of predatory urban and nationalist processes described above are imperative to develop effective counterstrategies at all scales.
Corporate-government collaborations drafted the 1998 Digital Millennium Copyright Act (DMCA), forging a cudgel now used to silence discourse in “incorrect” public spaces like the Cryptome library. We are a frequent recipient of DMCA take-down notices that reflect corporate enthusiasm for lucrative government contracts, and government reliance on outsourcing national security projects to corporate contractors. The corporate-government alliance otherwise known as Microsoft succeeded in shutting down Cryptome with a DMCA claim in 2010 – but only temporarily. Only relentless critique by watchdogs advocating for information equality can hope to expose the excesses of censorious business models that drive the enterprises of urban predation or national security wealth.
The processes of colonizing public space recall the enclosures that diminished England's agrarian commons in the 17th and 18th centuries. Parliamentary dicta evicted landless peasantry, rescinding their access to the commonweal of shared landscape and ushered in the key role of the modern nation state: defining and regulating private property rights, from fixed property as in real estate, mobile property –- that is, capital -– to intellectual property, and most recently, digital intellectual property, digital copyright, and so on. The sovereign classifications of national security State secrecy are in effect the most extreme categories of intellectual property's proprietary spectrum.
New York City reminds us every day how the corporate world has lustily collaborated in supplanting the public sphere with public-private partnerships that promote a dubious market model to interconnect philanthropy, non-profits, cultural products, tax law and offshore pre- and post-positioning of wealth. The Highline went from gritty relic of labor and manufacturing history to playground for a luxury-fixated quarter of the city whose cultural institutions are sleekly-saddled stalking horses for the global leisure class. One of our small educational clients and their modest lending library of books and pamphlets advocating against labor exploitation was driven out by rising rents.
It's mystifying that Laura Poitras should agree to commodify her so-called 'political' work in such a contaminated frame as the Highline district's new Whitney Museum with its $22 admissions fee, without problematizing the context. Similarly, First Look Media will be funding her new documentary projects under its banner of “smart, provocative entertainment.”
Cryptome continues looking to the urban street and online spaces of political sociality from below, where, as in the public library, no obligatory admission fee per se
is demanded.
〼IN THIS REGARD, PRESS MOGULS AND MEDIA CORPORATIONS HAVE AN IMPORTANT ROLE IN THE WAY IN WHICH CLASSIFIED DOCUMENTS ARE INTRODUCED AND TRANSLATED FOR GENERAL PUBLIC.
MANY OF THESE MEDIA OUTLETS SEEM TO EMBRACE THE IMPORTANCE OF TECHNOLOGICAL POWER THAT INTERNET PROVIDES TO DISCOVER GOVERNMENT ESPIONAGE TACTICS.
WHAT IS YOUR OPINION ABOUT THE WAY IN WHICH INTERNET AS A "FREEDOM OF SPEECH TOOL" HAS BEEN USED BY JOURNALISM IN THE LAST 10 YEARS? IS JOURNALISM AS A WHOLE STRUCTURE, AN ACCURATE PLATFORM TO RELEASE INFORMATION TO THE PUBLIC?
CRYPTOME: It's a half-hour walk up heavily trafficked Broadway from Cryptome to the Columbia Graduate School of Journalism at 116th Street, where Columbia University awards the Pulitzer Prizes each year. Prizes are announced to the sound of the media scrum's self-congratulatory fanfare. Cryptome has covered the Pulitzer ritual in the past and observes that the awarding of prizes for good works seems to assuage the anxieties of an ethically-challenged industry undergoing an identity crisis in a world of turbulent social and technological change.
New technologies may provide potential new tools in support of civil liberties like freedom of speech, but The New York Times will not relinquish its intimately symbiotic relations with chummy sources in the national security state. The Times sustains its support for civil liberties and freedom of speech with incongruously lurid advertising for luxury products: “Harry Winston, Rare Jewels of the World”; “Dior, Be-Dior bag in beige calfskin, details in goji pink patent calfskin”; “Come Home to Glenwood: Manhattan's Finest Luxury Rentals -- white glove service, magnificent lobbies, near the best NYC schools.”
We note Columbia Journalism School reports the 2016 cost of its prestigious 10-month Master of Science degree, including living expenses, is $97,603: “As a student in our Master of Science program, you'll learn how to think critically and be both ethical and street smart.” By embracing business best-practices, the corporatized elite university caters to the student as a luxury consumer, just as it improves its institutional bottom line by exploiting a just-in-time army of underpaid adjunct instructors.
Any consideration of professional journalism as a whole structure, as Tecno|Grafia[s]
refer to it, would have to include this astonishing price tag for entry level access, and the substantial student debt incurred. What career choices will the debt-laden young journalist -– or architect, lawyer, physician -- be forced to make going forward? Can such a precariously front-loaded platform offer stable support to the public commonweal? It is well documented that student debt suppresses risk-taking by increasingly compliant young practitioners.
We once overhead a Columbia journo student on the Broadway M104 local bus insistently remind a companion who was touting a rival journalism program that Columbia was, after all, “the Pulitzer school!”
Sadly, Pulitzer prestige seems to play a seductive role inducing student to incur debilitating debt to gain privileged admission into a competitive profession.
Vigorous investigative reporting by definition must bite the hand that feeds it. In the front-loaded platform described above, the feeding hand gets the upper hand when threatening retaliation against a vulnerable reporter. Investigative journalists like Seymour Hersh are accused of 'going too far' within corporate journalism that draws a cautious bottom line around what constitutes practices of critical investigation.
Given these constraints, can the public trust the journalism or any profession, even independent journalism, to be the fair broker of the commonweal it claims to be? It's no surprise that both the DocumentCloud and the New York Police Department office that issues press cards refused Cryptome's application for press credentials on grounds of ineligibility.
〼 MAYBE THE MEDIA IMPACT OF MAINSTREAM FIGURES LIKE MANNING OR ASSANGE IS ONE OF THE FIRST ENCOUNTERS THAT MANY PEOPLE HAD TO UNDERSTAND A CERTAIN IDEA CONCERNING MASSIVE ESPIONAGE, BUT THAT DOESN'T MEAN NECESSARILY THAT DOCUMENTS ARE BEING ANALYZED IN A CRITICAL OR AN ONTOLOGICAL SENSE AS DEBORAH RECENTLY DECLARED. THIS PROCESSED NARRATIVES HUGELY EMBRACED BY MEDIA ALSO, AS YOU FORMULATED BEFORE, ARE THE PERFECT OPPORTUNITY TO SIMULATE OPPOSITION, TO CONFIGURE THE PUBLIC IDEA OF RHETORICAL DISCUSSIONS BETWEEN RIVAL DISCOURSES.
ARE THOSE STRATEGIES THE MAIN RESOURCE FROM MEDIA CORPORATIONS AND NGOS TO MAKE PROFITS AND REPUTATION FROM DOCUMENT LEAKS? IS NAIVE TO PRETEND THAT EFFECTIVE ALTERNATIVES AND TECHNOLOGIES TO KNOW HOW POWER SPHERES SPY ON US ARE POSSIBLE?
CRYPTOME: What constitutes innovative opposition and what is a form of kabuki theater whose actors assume stock poses to elicit programmed audience response? It's regrettable that as a matter of business sustainability, independent media's internal traffic analysis seems to have persuaded it to master the rhetorical intricacies of a hyped product roll- out in which stock rivalries are hardwired into formulaic scripts. The leak reporting industry has sprung up as a niche market with just such increasingly familiar roll-out strategies.
The 2016 US presidential election season demonstrates yet again that dramatizing rivalry is an effective media tactic as well as fundraising tool. Sports-saturated American culture responds to competition metaphors and racecourse similes. On the campaign trail, fundraising letters are issued immediately following a manufactured fracas and the tally of monies received within 24, 48 or 72 hours breathlessly announced as if a triumphal box-office take.
On the other hand, when Cryptome was briefly shut down by Microsoft's DMCA claim in 2010, the unexpected surge of donations from supporters that suddenly came pouring in was summarily confiscated by Paypal –- under their red flag alert for suspicious or terror-related financing. Cryptome subsequently instructed that all monies be returned to donors.
What agency do networked, non-professional individuals have within what has become such a highly compromised media business model? We're sympathetic to Hardt and Negri's optimism about the possibility of the multitude's self-determining commons. Cryptome's approach as a small scale networked library practicing information equality 'from below' may be an experimental gamble, but it's a gamble we take nonetheless.
A few weeks before 9/11, we gave an invited talk in Washington DC at the 10th Security Symposium of USENIX, the Advanced Computing Systems Association. Our talk Reversing the Panopticon introduced for the first time the concept of reverse-engineering Bentham's iconic socio- political architectonic. (Others have since adopted our locution.) The technical and cultural skills required for the architect to decrypt and integrate complex building codes, contract documents, architectural drawings and detailed material specifications within the negotiated practicum of the construction field provide an operational toolkit for Cryptome's incremental project of small scale reverse-engineering towards the goal of the information equality library. Others can experiment with different toolkits towards similarly creative outcomes.
〼9/11 WAS A KEY MOMENT IN THE HISTORY OF USA, ESPECIALLY IN A FINANCIAL AND CULTURAL NUCLEUS LIKE NEW YORK.
THE CITY LIVED IN A RENEWED AND CONSTANT SURVEILLANCE STATE ACHIEVED THROUGH AGGRESSIVE POLICING TECHNOLOGIES OF BIO-TRACKING, INFORMATIONAL INTERFERENCE, ETC. WHAT IS THE NEXUS THAT ATTACH THE USE OF POLICING TECHNOLOGIES, YOUR RESEARCH ON THE NYPD RING OF STEEL AND THE COLD WAR? HOW 9/11 AFFECTED CRYPTOME AND YOUR PRACTICE AS ARCHITECTS BASED IN NEW YORK?
CRYPTOME: John and my personal experiences empanelled as members of the jury pool on trials in New York City Federal and State court are reflected in Voir Dire, a project that maps the network of surveillance sensors installed around Lower Manhattan after 9/11 by the New York Police Department (NYPD). The extensive security apparatus is informally referred to as the Ring of Steel as an homage to London's predecessor system. Voir Dire questions the civic impacts of counter terrorism security theater -– the panoply of bulletproof vested guards, automatic weapons, vehicular delta barriers, surveillance cameras etc –- on prospective jurors from underrepresented communities arriving at the civic center courthouses that lie in the nucleus of the security Ring.
The late African-American US Supreme Court Justice Thurgood Marshall
, for whom one of these courthouses is named, 'suggested that unrepresentative juries not only cast doubt on system legitimacy but also influence deliberations and verdicts.' A 2007 study by Citizen Action of NY concluded racial and ethnic disparity in Manhattan jury pools calls into question the fairness of verdicts. Voir Dire asks whether democratic processes can flow unimpeded across a juridical landscape dominated by aggressive policing technologies and iconography – when the viability of such democratic processes urgently require the participation of underrepresented jurors from marginal communities already subject to hostile policing.
At the heart of this question is our critique of the extrajuridical practices which make Guantanamo an opaque doppelganger of New York's juridical city. Some Guantanamo prisoners would have faced prosecution within the due processes of NYC courts had they not – under exceptional claims of a national security state of emergency – been displaced to the untested legal procedures of that extraterritorial, blackened site. The adjudicative chaos surrounding Guantanamo is intimately connected to the Ring of Steel apparatus as interlocking features of a failed civic architecture.
Jurors from New York City's global South immigrant communities are among underrepresented communities of the jury pool locked in cross hairs of the NYPD Intelligence Division. The Division was hardened after 9/11 into the largest and best funded police intelligence branch in the US. NYPD is always searching for a Molenbeek lurking in the city's Muslim neighborhoods.
We remind readers that David Cohen, the powerful first post-9/11 NYPD Deputy Commissioner for Intelligence (2002-2013), was a former senior official of the CIA responsible for its world wide operations. Cohen actively maintained insider links to the CIA during his NYPD tenure. Consistent with the trend to militarize policing described by geographer Stephen Graham, the NYPD Intelligence Division and NYPD Counterterrorism Bureau recruit officers with military and intelligence backgrounds.
The culture of the CIA, with origins in Cold War technologies of secrecy, surveillance and proxy warfare are part of the legacy Cohen infiltrated into the policing of a global city whose regulation has in many ways superseded the scale of the national. The International Liaison Program supports policing at global scale by placing NYPD intelligence officers in 11 overseas cities. The liaison program evades robust public oversight by securing funding from private business, individuals and philanthropic partners laundered through a public-private partnership, The New York City Police Foundation.
Voir Dire advocates for the underrepresented juror we refer to as 'the barely juror' as a key actor in public space urgently required to reverse these increasingly redacted processes of public oversight and public adjudication. Such public reversals reinforce the bedrock of information equality.
〼 PARALLELY, AFTER TWO DECADES OF CRYPTOME’S EXISTENCE, INTERNET’S STRUCTURE AND ITS ECONOMIC SURPLUS HAS CHANGED NOTABLY.
WHAT ARE THE MOST COMMON TECHNOLOGIES TO SPY AND HOW THEY CHANGED WITH THE ARISE OF COMMERCIAL STRATEGIES LIKE THE INTERNET OF THINGS?
CRYPTOME: Surveillance theorist David Lyon warns about the dangers of 'social sorting' that is a consequence of data mined from commercial mass surveillance, in addition to the political sorting conducted by government mass surveillance seeking political or military targets. Relentless commercial tracking of consumer habits is a persistent tool in developing market-driven strategies for extreme socioeconomic stratification.
A recent article in the New York Times confirms that “companies are becoming adept at identifying wealthy customers and marketing to them, creating a money-based caste system”. Pointing out that such social and economic stratification has been unseen in America since the Gilded Age of industrial robber-barons at the turn of the 19th century, the Times notes “the goal is to create extravagance and exclusivity for the select few, even if it stirs up resentment elsewhere. In fact, research has shown, a little envy can be good for the bottom line.” The 2016 US presidential election cycle has exposed the impacts of stirring up long-simmering resentment about income inequality.
With its rigorous tracking of consumer desire, the omniscient Internet of Things cannot avoid functioning as a commercial tool for pernicious social sorting. Data from ubiquitous IoT sensors have become the red ink of redlining practices writ large. Another NY Times article reports “self-segregation of a privileged fifth of the population is changing the American social order and the American political system, creating a self-perpetuating class at the top, which is ever more difficult to break into.” IoT technologies self-perpetuate inequality while accelerating self-segregating geographies of global wealth as their sensors report minute spatio-temporal data from high-end automobiles, stainless steel refrigerators, in-ground swimming pool gadgetry and personal tablets used by luxury households to communicate via satellite with other family members who are ensconced in private bedrooms just a few meters away.
〼 CRYPTOME DOESN'T SELECT OR GUIDES USERS IN THE RESEARCH, USE OR INTERPRETATION OF THE DOCUMENTS PUBLISHED, IS INTERESTING TO ANALYZE HOW THE STRUCTURE OF THE WEBSITE SUBVERTS THE WAY IN WHICH WE READ, INHABIT AND DOWNLOAD DIFFERENT POLITICS OF INFORMATION. THERE’S A REASON TO IMPLEMENT THIS MODE OF AVAILABILITY.
CRYPTOME: Cognitive-cultural capitalism sanctions curating as a high-end service integral to activities of branding, marketing and profiting. All these rely in equal parts on passivity as a correlative of consumer desire.
We reject the curator-marketer and instead hope to nurture reader autonomy, self- awareness and choice we believe integral to the dyad of self-knowledge and self-rule. The reader's activist participation encourages a state of becoming through self-guided learning and networked feedback loops.
John and I used to teach occasionally in graduate architecture programs but withdrew as corporatization colonized the American university and began crushing students into the penury of massive student debt discussed above. We prefer modest, self-guided DIY cultures of repair to shiny new institutional packaging. Cryptome's anti-curated online collection is still formatted in the original raggedy columnar structure and generic Courier font of 1996, authored on a thoroughly obsolete AOL Press html platform. We hope this arte povera
approach encourages others to contribute universal DIY tools for achieving information equality and an expanded public domain.
〼 THE EXPOSURE AND POPULARIZATION OF SURVEILLANCE TECHNOLOGIES IN THE LAST 8 YEARS COULD BE CONCEIVED AS A POSITIVE ADVANTAGE ABOUT THE OPENNESS/ABUSE OF GLOBAL GOVERNMENTAL ESPIONAGE TACTICS. NEVERTHELESS, THIS MEDIATED AND ELABORATED PERCEPTION SUGGEST THAT THE MASSIVE LEAKS OF DOCUMENTS SAW THE LIGHT WITHOUT INTERMEDIARIES. YOU’VE BEEN VERY CRITICAL ABOUT THE WAY IN WHICH THE SNOWDEN LEAKS HAVE BEEN RELEASED, ESPECIALLY BECAUSE THE DOCUMENTS ARE NOW ADDED INTO A NEOLIBERAL MODEL TO GET ECONOMIC INCOMES THROUGH BOOK DEALS, FILMS, ART EXHIBITIONS, NEWS PLATFORMS, ETC. IN THIS FRAME, WHAT DO YOU THINK ABOUT GLENN GREENWALD AND LAURA POITRAS ’TRANSPARENCY’ DISCOURSES TOWARDS THE SNOWDEN DOCUMENTS?
CRYPTOME: Glenn Greenwald reveals in No Place to Hide that when it seemed there was a chance The Guardian might not publish his first articles from Hong Kong about the Snowden NSA documents, he considered creating NSAdisclosures.com, a website where articles could be released without the help of existing media outlets by using volunteer editors, lawyers, researches and financial backers. At the end of the day, as we know, Snowden's deal was negotiated within existing media's more conventional frameworks. The fine print of the deal remains a mystery. As for the domain NSAdisclosures.com, some unknown person subsequently acquired it and now, quite irreverently, automatically redirects to the SnowdenTally project Cryptome initiated in October 2013 to keep tabs on journalism's handling of the Snowden cache. Amusingly self- referential!
What would have become of the Snowden material had NSAdisclosures.com launched as an independent experimental platform for robust archiving and distribution? This question reminds us that Cincinnatus was one of Snowden's chosen aliases during his initial contacts with media, referencing a Roman who, we're told, used political power in the public interest. How vigorously has the public interest been served by the journalistic strategy implemented to validate and regulate the NSA disclosures, from early Guardian articles to the waning output at The Intercept and the rising First Look Media entertainment complex?
Greenwald claims Snowden “stressed that it was vital to publish the documents journalistically – meaning working with the media and writing articles that provided the context for the materials, rather than just publishing them in bulk.” We're told Snowden believed this would be the more orderly, more rational approach. After all, he was to have stated, he could have published the NSA material en masse himself. Finally, Snowden felt journalistic responsibility would minimize risk of harm to innocents caused by the revelations.
Journalism's status as the “responsible” sine qua non of public interest needs to be vigorously debated as long as Snowden continues to make demands for proprietary control of 'his' taxpayer-funded trove, including through instructions to media proxies. It's possible he may intend to surrender the balance of the files to the US government in exchange for prosecutorial leniency and the chance to return to the US from his Moscow exile. After calling for full disclosure of the NSA cache for some time, we're pleased that The Intercept released a new tranche of files in May 2016.
Nevertheless, Snowden evidently rejected more experimental modes of distribution by self-organizing multitudes in favor of what, in retrospect, appears to have turned out to be a cynical journalistic process of maximizing curatorial control over the goose named Exclusive Scoop in order to claim all her golden eggs – including full spectrum product tie-ins from publicity, celebrity, accolades and awards to movie rights and royalties. Cryptome recently obtained documents from the public record that reveal Greenwald's 2015 base salary at the non-profit The Intercept to be $490,000. This is hardly consistent with the acts of civic humility attributed to Cincinnatus.
〼IT SEEMS THAT INSIDE 21ST CENTURY'S COGNITIVE CAPITALISM, THERE'S A DESIRE TO TRANSCEND INSIDE THE BIG NARRATIVES (& MARKETS) OF OUR TIME.
WHAT IS YOUR OPINION ABOUT THIS MODE OF NARRATIVE-INCLUSION THAT OBEYS TO A DESIRE TO BE LEGITIMIZED AND RECOGNIZED INSTITUTIONALLY? (AGAIN, MAYBE IS UNNECESSARY TO SUGGEST A DISCUSSION BASED IN THE ALWAYS- RECURRENT GREENWALD/POITRAS CASE AS A MODEL.)
CRYPTOME: Churning the account refers to the illegal practice by brokers making excessive trades on client accounts in order to reap undeserved commissions.
Cryptome sees ample display of the media churning the marketplace of trending narratives to skim commissions off the top, including in the leak reporting industry that has sprung up in the hopes of fostering a lucrative niche market. While perhaps not illegal, this practice illustrates the losses suffered by robust investigative journalism against the rising tide of click-baited infotainment.
Whenever Cryptome has been even tangentially implicated in a rising narrative or a cannily mediated product rollout such as “the Wikileaks story” for example, a flood of press inquiries of shallow, repetitive banality is unleashed on us. Substantive public education is not a goal of the bottom line. Rather, media outlets churn the account of narrative tsunamis to artificially amplify wave effects and capture hoped-for revenue streams. Has this pattern as currently built into protocols for conducting a successful leak in the so-called public interest run its course? Can alternative platforms be advanced?
CRYPTOME: We welcome the vigorous exchange of ideas hosted by Berliner Gazette at Transmediale 2016. At the same time, Cryptome's experience as a practice unaffiliated with academic institutions, NGOs, large non-profits and their respective funding streams and sociologies of expert knowledge means we continue to rely on feedback loops from below to sustain the site's discursive field.
Transmediale premiered our 20 minute visualization ± False Tallies: The Prisoner's Dilemma a narrative work that introduces an historical context for Cryptome's Snowden Tally, which, since October 2013, has been keeping tabs on the media's proprietary roll-out of the Snowden archive.
Because Edward Snowden remains something of a dilemma-plagued prisoner of Moscow, ± False Tallies engages him in a hypothetical instance of the classic Cold War game theory scenario called The Prisoner's Dilemma. We partner Snowden across time with Nikolai Khokhlov, a Soviet NKVD/MGB military intelligence agent and occasional assassin who defected to the West in 1954.
We believed Snowden and Khokhlov make an interesting game theoretic partnership. Each underwent ruptures of their respective national identities as highly mobile, multiply-aliased engineers of nation-state border control. Each ended up exercising autonomy, agency and dissent – and shed the authority of state aliases for post- national identities constructed within private spaces of their personhood. ± False Tallies considers the dilemmic choices unfolding within their respective historical and technological cartographies of nation-state border rupture, from Khokhlov's East-West territorializations to Snowden's role regulating nation-state sovereignty in the 21st century's increasingly borderless world.
± False Tallies also touches in passing on some site-specific aspects of Transmediale's provocative architectural milieu in Berlin's Tiergarten, the 1957 Cold War structure now called Haus der Kulturen der Welt (HKW). We recognize the design of HKW as a rhetorical construct of architecture parlante within the Cold War diplomatic culture of John Foster Dulles, the US Secretary of State (1953-1959), after whom the tree-lined boulevard out front is named.
More subversively, however, we link the engineering of this former Kongresshalle to what we dub an architecture écoutante of signals intelligence technology engineered during the tenure of that diplomat's clandestine brother, Allen Welsh Dulles, director of CIA (1952-1961). We detect Snowden and Khokhlov's post-national, performative selves as rogue emanations escaping covert streams of clandestine signals intelligence. Cryptome will support any effort to rename the boulevard Allen-Welsh- Dulles-Allee, certainly whenever the annual Transmediale is in session.
〼 A COMPANION SITE OF CRYPTOME, TITLED CARTOME (ADMINISTRATED BY DEBORAH NATSIOS) FOCUS ON ARTWORKS THROUGH CRITICAL AND INTERACTIVE CARTOGRAPHIC DEVICES. AESTHETICALLY IS ONE OF THE MOST INTERESTING NON-BOUNDARIES STRUCTURES THAT CO-EXISTS IN THE SITE, ADDRESSING MULTILAYERED GEOPOLITICAL AND NATIONAL SECURITY TOPICS.
EVEN WHEN THE PROJECTS CONTAINED IN CARTOME HAVE THEIR OWN MICRO-ANALYSIS, EVERY ONE OF THEM SHARE SIMILAR LINES ON “SPATIAL / GEOGRAPHIC DOCUMENTS ON PRIVACY, CRYPTOGRAPHY, DUAL-USE TECHNOLOGIES, NATIONAL SECURITY AND INTELLIGENCE -- COMMUNICATED BY IMAGERY SYSTEMS: CARTOGRAPHY, PHOTOGRAPHY, PHOTOGRAMMETRY, STEGANOGRAPHY, CAMOUFLAGE, MAPS, IMAGES, DRAWINGS, CHARTS, DIAGRAMS, IMINT AND THEIR REVERSE-PANOPTICON AND COUNTER-DECEPTION POTENTIAL...”
MANY OF YOUR PROJECTS ARE RELATED WITH THE GLOBAL USE AND DISTRIBUTION OF TECHNOLOGIES SINCE THE COLD WAR.
〼 WHAT IS THE EVOLUTION OF DUAL-USE TECHNOLOGIES AND WHAT IS THEIR ACTUAL IMPACT ON INDIVIDUAL’S CONSCIENCE ABOUT SURVEILLANCE? WHY YOU DECIDED TO OPEN AND EXPAND THIS AUTO(BIO)GEOGRAPHIC SPHERE? WHAT MOTIVATED YOU TO TAKE AESTHETIC AND POLITICAL RISKS WITH THIS PRACTICES?
〼
HOW DIFFICULT WAS THE RESEARCH PROCESS FOR CITY OF REDACTIONS? CAN YOU EXPLAIN HOW THE NEOLIBERAL CITY OPERATES IN THE VISUALIZATION OF NON-CITIZENS?
CRYPTOME: It's somewhat amusing that Cartome's interest in reverse-panopticon and counter- deception mapping has its origins in beetles I started collecting at architecture school as coleopteran proxies for my past and future geolocations. The presence of fantastical exoskeleta in the architecture atelier distressed more than a few entomophobic classmates and instructors.
Highly adaptive species native to the politicized landscapes traveled during my childhood became carapaced alter egos offering myriad chitinous aliases for exploring the space of world politics.
Beetle avatars helped structure a geographic information system to orient the Entomofilia Atlas, an aliased autobio(geo)graphy of taxonomic borders investigated in pencil, charcoal and cut paper. Before going underground and vanishing altogether, coleoptera continued to occupy later digital mappingworks like Parallel Atlas 39°N and L'Empire des Oiseaux. Textual fragments embedded in these later micro-histories are map legends written 'from below' to unlock auto(bio)geographic codes as guides for diasporas swarming across heavily regulated childhood borders in Cold War Greece, Korea and Vietnam. The decryptions of Parallel Atlas 39°N informed our work in support of The DMZ Forum, an international group advocating for the peaceful preservation of the Korean Peninsula's biodiverse Demilitarized Zone, an iconic Cold War relic, as a transboundary conservation park.
Because biogeography tracks the geographic range and distribution of species as components of taxonomic systematics, it offers metaphoric ways to challenge the reductive classifications of Cold War border institutions limited to geopolitical blocs of East, West or Non-Aligned. Granular, counter-cartographic landscapes attempt to dislodge dominant geopolitical narratives that polarized US 'containment' doctrine's more iconic borderlands.
The Cold War border series provide an historical context for more recent investigations of nation-state border security being litigated around the crisis of the borderless state. As you can see from its index page, Cartome
was archiving geospatial documents largely related to the militarized aspects of this research during 2001-2002. After 9/11we shifted focus to authoring longer-term, integrative cartographic projects.Our most recent integrative projects investigate risk management tools that have replaced containment doctrine to anticipate surges that are flooding borders in military and policing contexts as well as in marketplaces of the neoliberal city. The crossover efficacy of dual-use technologies (with military and civilian applications) reflects the current neoliberal symbiosis of military and commercial interests.
Cold War doctrines and technologies of bipolar containment explored in earlier maps have yielded to 21st century states of emergency, doctrines of preemption and anticipatory governance that rely on ubiquitous mass surveillance
and Big Data analytics to regulate risk for future outcomes. Discrete personhood is risky when it projects dissenting self-rule into a future that Long War theory declares will surely be dystopian.
MEET-ME at your Riser (2013) visualizes post-national regulation of the political border as displacements from the nation-state's traditional geographical boundary to telecom colocation centers where transborder flows of global communications are managed. Global networks exchange data in New York City's colocated meet-me rooms at 32 Avenue of the Americas (32 AoA) by physically interconnecting fiber optic lines routed from transatlantic cables into the underground conduits that are telecom backbones of the city. MEET-ME at your Riser considers a legal case that exposed NSA secure rooms installed in telecom hub buildings to illegally intercept internet traffic. As the state of emergency's displaced border control booths, these militarized secure rooms defend the sovereignty of the nation-state by interdicting presumably risky cross-border communications – in legal disregard of fundamental civil liberties.
Cryptome's toolkit as architects was instrumental in this example of reverse-engineering the current status of 32 AoA, a landmark communications building originally completed in 1932 for use in then state-of-the-art long line telephony.
〼 IT’S NOT SURPRISE THAT YOU’VE BEEN CENSORED BY DIFFERENT INSTITUTIONS FOR YOUR STATEMENTS ON URBAN PREDATORY ACTS, CORPORATE, POLITICAL AND ECONOMIC INTERESTS, ETC. IN 2013, PARTY WALL: BOWERY DIALOGUES, A SERIES OF ARTWORKS FRAMING A DIALOGUE BETWEEN THE BOWERY MISSION (A RESCUE MISSION AND MEN'S SHELTER) ANDTHE NEW MUSEUM OF CONTEMPORARY ART WAS REMOVED AND CENSORED, THE ARTWORKS MADE VERY CRITICAL DISCLOSURES ABOUT THE REAL INTENTIONS BEHIND NEW MUSEUM’S IDEAS CITY FESTIVAL (GENTRIFICATION, COLONIZATION, RACISM, URBAN CLEANING, ETC.) WHICH WERE THE MAIN REASONS FOR THE NEW MUSEUM TO CENSOR THIS SERIES LOCALIZED IN THE BOWERY MISSION BUILDING?
WHAT IS YOUR OPINION ABOUT THE WAY IN WHICH GLOBAL ART INSTITUTIONS OPERATE IN THE ECONOMICAL RE-DESIGN OF A CITY?
CRYPTOME: The New Museum proclaims the biennial IDEAS CITY festival it installs across its Bowery neighborhood “explores the future of cities with culture as a driving force.” As Tecno|Grafia[s] notes, on the eve of IDEAS CITY 2013 our street-front exhibition Party Wall: Bowery Dialogues a series exploring the relationship between The New Museum and its direct neighbor, The Bowery Mission, was summarily taken down after being on display only 48 hours.
Mounted at the invitation of the venerable rescue mission that has served homeless and hungry New Yorkers since 1879, the work examined the relationship between the two adjacent institutions by posing questions about hunger, housing insecurity, colonization, the criminalization of urban loitering vs. the sanctification of art viewing, and the false consciousness of the museum experience.
The incident offers a useful case study to expand our prior observations about pedestrian mobility as tool of urban investigation. New York City's public street offers critical vantage points for documenting market encroachments on what remains of urban public space understood as intensely social places, including of potential democratic dissent. The censoring of our street-front critique of culture from a festival that invites ideas about “the future of cities with culture as a driving force” is a case in point.
For over a year leading up to The New Museum festival we had been involved as professional architects for the Bowery Mission, reconstructing underground vaults to provide structural support for its landmark nineteenth century facade and public sidewalk. The project advanced our commitment to public health, public safety and public welfare (HSW) values invested in behind-the-scenes rehabilitation of decaying urban infrastructure. One of our areas of expertise demonstrated in this project was the control of leaks –- that is, leaks in the moisture-protection sense!
Our underground structural work at the Mission helped stabilize the collective public domain for the homeless who embody intensely specialized local knowledge of the exclusionary city. They travel challenging itineraries to join the common queue that metabolizes daily along the public sidewalk in front of the Mission where a free midday meal is offered. The queueing of the disenfranchised is a compelling street performance directed at public education. It draws from a performative repertoire that includes spontaneous recitations and dialogues about life within the extreme stratifications of a city where cultural institutions avidly complete circuits for global wealth. Party Wall details our architectural postscript for a structural stabilization project completed in the context of extreme social and economic destabilization. A subsequent video visualization, Bowery Ghost Ships further advanced this narrative.
The Bowery's transformation in recent years from notorious quarter of derelict rooming houses into an exclusive residential zone for high-end cultural thrill-seekers threatens to censor the queue's narrative act, however. Squeezed by a new boutique hotel to its south and The New Museum to its north, the Bowery Mission queue as embodied performance of lives lived under duress -– as political speech -– may have no future on a sidewalk being privatized as a consumer delivery system to access luxury retail stores, posh residences and expansionary cultural institutions. The queue is already invisible to hip museum-goers rushing to legitimate their cultural credentials at the next blockbuster show.
The city of cognitive-cultural capitalism regulates products in its cultural marketplace with nuanced intimidation. We learned that one veiled phone call from a New Museum IDEASCITY organizer to The Bowery Mission questioning the Party Wall installation was enough to cow the fragile welfare institution into neighborly capitulation. Gentrification relies on such iron-fist-in-velvet-glove acts of oblique persuasion.
In May 2016, a notorious landlord specializing in illegally evicting rent-regulated tenants from gentrifying buildings of the Lower East Side neighborhood the museum calls home was indicted on 20 felony criminal counts. How many hipsters on the membership rolls of The New Museum are among new tenants who gladly paid higher rents, no questions asked, for apartments illegally vacated by needy, long-term occupants and subsequently deregulated from rent-stabilized status as a result of criminally destructive acts?
The digital take-down of the Cryptome site in 2010 by Microsoft's DMCA notice provoked waves of support by information activists. Following the take-down of Party Wall, however, many culture workers fully dominated by high-profile cultural institutions looked the other way. A spokesman for the New Museum officially denied any role in the incident.
At the same time, the New Museum announced in May 2016 it will double its footprint by expanding into an adjacent building, and also plans to expand its IDEASCITY support space. The museum bloat smacks of a cultural lebensraum that justifies all invasive prerogatives. Information activism offers strategies to challenge predatory urban “driving force” whether self-described as cultural or not.
〼 IN YOUR EXPERIENCE, WHAT IS REAL SCOPE OF PROTECTION OF ENCRYPTION TECHNOLOGIES AND WHO ARE BEHIND THE REINFORCEMENT OF THIS TOOLS?.
TO PUT MORE EMPHASIS, THE ORIGIN OF THIS QUESTION IS ROOTED IN AN EXCHANGE OF TWEETS BETWEEN JACOB APPELBAUM AND JOHN YOUNG, DISCUSSING ABOUT THE RELIABILITY OF TOR.
CRYPTOME: Encryption issues debated by the renegade Cypherpunks coders John became involved with in the early 1990s provided the framework for our founding Cryptome in 1996. At the time, cryptography was a controversial technology included until 1992 on the U.S. Munitions List as Auxiliary Military Equipment.
Any insights we contribute to next-generation encryption debates in the 21st century are informed by a timeline that begins with the US government launch of a three year investigation targeting Phil Zimmermann, the coder of PGP encryption software he made available for general use in 1991. Before the investigation was dropped in 1996, the government invoked the Arms Export Controls Act against Zimmerman after PGP began to be distributed online to worldwide users.
Interestingly, John took the forward-looking step in 1995 of nominating Zimmerman's coding of PGP for a Chrysler Award granted by the automotive corporation to innovators in more cultural contexts like architecture or industrial design. Radical coding was hardly considered to be cultural production at the time. John's argument was evidently persuasive and Zimmerman was indeed awarded a $10,000 prize while still under government investigation.
More conventional definitions of culturally innovative design are evident in another Chrysler Award that happened to be given out that same year to Frank Ghery, the architect whose Guggenheim Bilbao would be inaugurated in 1997. The contrast between the radical utility of PGP deployed worldwide -- often in liberatory contexts -- Zimmerman's own personal risk, and the scenographic starchitecture that is Ghery's Bilbao could not be a more stark.
Cryptome's questions about possible security conflicts in Tor's anonymizing onion routing, given its origins at the US Naval Research Laboratory and its current government funding, continues our preference for robust inquiry provoked by pragmatic skepticism and doubt. Our interest in forensic detail evolved during the 1990s when the so-called Crypto Wars were vigorously litigated, when we attended those seminal trials held in New York City's jurisdiction, and more broadly, began the habit of purchasing court documents related to landmark crypto and digital intellectual property cases at our own expense and making these available online. Cases like Bernstein v. United States (1995), Junger v. Daley (1996), The Digital Millennium Copyright Act (1996) and MPAA v. 2600 (2000) helped establish the slowly-accruing legal basis for the HSW infrastructure of Cryptome's modest public library for information equality.
〼 TWO IMPORTANT MEDIA COVERAGES INVADED NEWS OUTLETS THE LAST WEEKS, THE PANAMA PAPERS AND BLOOMBERG’S HOW TO HACK AN ELECTION.
WHAT ARE YOUR THOUGHTS ABOUT THE INTENTIONS AND IMPACT OF THE PANAMA PAPERS? YOU ALREADY KNEW ABOUT OTHER SIMILAR CASES OF HACKING ELECTIONS LIKE THE CASE OF ANDRES SEPULVEDA?, AND IF SO, THIS ARE OLD STRATEGIES TO MODIFY THE COURSE OF AN ELECTION?
CRYPTOME: We appreciate your question about breaking news as an opportunity to emphasize the open-ended, fast-moving nature of our project. It's a way to look forward to continuing our dialogue into the future. We'll leave it at that for now ...
CRYPTOME [DEBORAH NATSIOS + JOHN YOUNG] INTERVIEWED BY H C-(M)
/ EDITION + GRAPHICS: CRYPTOME + H C-(M) _ 2016